We offer Extensive, cost effective and flexible automation and self-service capabilities, so you can concentrate on delivering business value.
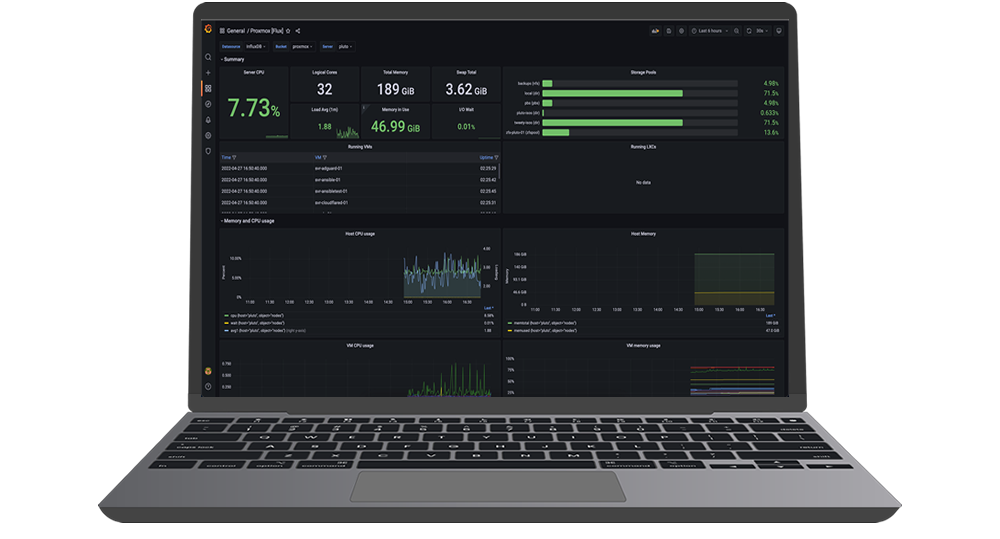
We protect your organization’s digital assets through advanced cybersecurity measures, performing tasks like constant monitoring and threat detection
A cybersecurity strategy that utilizes multiple security measures to protect a network or a private cloud from attacks
We use a structured process to manage and respond to any threats, like breaches or cyberattacks by minimizing damage and restoring normal operations
It is a fundamental building block of cybersecurity, ensuring that data cannot be read, stolen, or altered either at rest or in transit
It is an important measure to predict and prevent by fixing security gaps before they can be exploited and mitigate their highest risks
Our fully qualified L2 and L3 teams work 24/7 to assist you in every possible situations & circumstances and diffuse all possible threats
Organizations must prioritize compliance to address security concerns, manage reputational risks, and maintain integrity
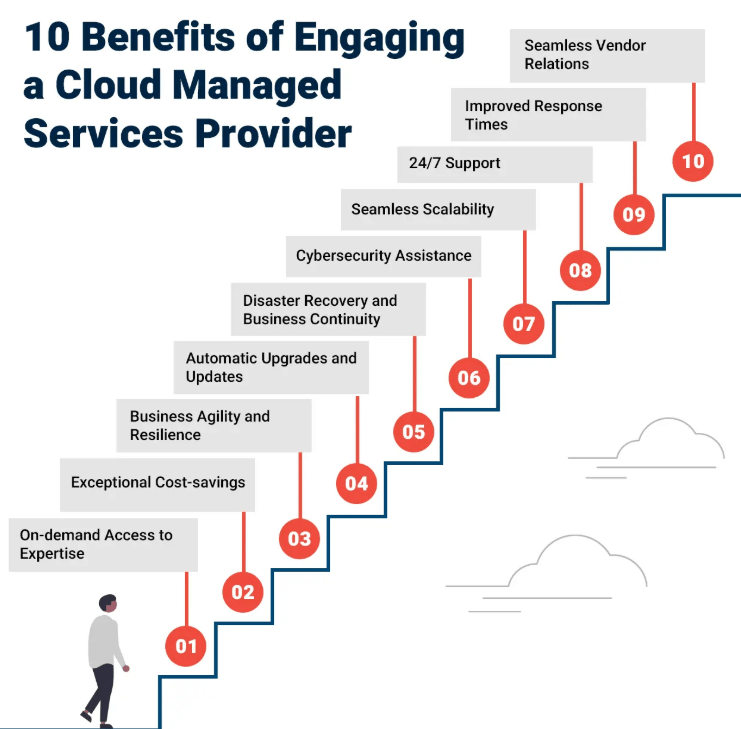
In addition to addressing a number of landscape challenges, managed security also offers organizations many important benefits. These include:
Organizations that operate in the cloud recognize that their data, applications, and networks constantly face countless threats and challenges, including the following:
As technology continues to evolve, organizations need to accelerate their digital trajectories to provide measurable benefits for their customers. But, to constantly innovate and drive their strategy, most do not have the IT capabilities, bandwidth, or resources to strike the perfect balance between their business and technology needs. Here is why we come-in in crafting your technical operations.
MDR remotely monitors, detects, and responds to threats detected within your organization. Relevant threat intelligence, advanced analytics, and forensic data are passed to human analysts, who perform triage on alerts and determine the appropriate response to reduce the impact and risk of positive incidents. Finally the threat is removed. The core capabilities of an MDR are: